The Shentu Chain is working hard on redefining the standards of security and trustworthiness in the Web3 space. Developed by the Shentu Foundation, Shentu Chain is a Delegated Proof-of-Stake (DPoS) blockchain built on the Cosmos SDK. It is a secure foundation for building blockchain infrastructure and decentralized applications (dApps). With its on-chain features, such as the Security Oracle, ShentuShield Reimbursement Pool, and the use of a secure programming language called DeepSEA, Shentu Chain ensures the security of various blockchain products throughout their lifecycle. So, let’s have a further look at the Shentu Chain and its most important elements.
Understanding Shentu Chain
Shentu’s mission is to empower people to trust blockchain and its technology by utilizing cutting-edge technology and techniques that prove trustworthiness in underlying systems—hoping to raise the standard of security and trust in the Web3 space. So, where did Shentu Chain get started? In June 2016, the Ethereum Network faced a significant attack when The DAO, an early ICO project, was hacked due to a smart contract flaw. The hacker drained $1.2B worth of ETH, leading to The DAO's downfall. Then, Ethereum underwent a hard fork, resulting in Ethereum (ETH) and Ethereum Classic (ETC). This is one the first of many small and big incidents within the blockchain ecosystem that highlight the ongoing battle between developers securing the crypto space and hackers finding new ways to exploit vulnerabilities and steal assets.
In the world of smart contracts and on-chain protocols, security analysis heavily relies on centralized organizations known as security auditors. These auditors conduct varying levels of audits, providing crucial information about the code's reliability. However, there's a significant problem: these analyses are often inaccessible when needed the most, right before completing a transaction. Smart contract users are left to do their research (if they can access the audit reports) to determine if their assets are safe. That places early adopters at significant risk, who should be valued the most, as they need more time and technical expertise to interpret the security analysis.
The Shentu team (initially under the name CertiK) decided it was time to come up with a solution, thus aiming to change the current situation by providing provable trust for all users. Giving users immediate access to on-chain, decentralized security intelligence at any time. That’s how Shentu became a comprehensive security solution for the blockchain ecosystem. Using their Security Oracle, ShentuShield reimbursement protocol, and the highly secure smart contract programming language DeepSEA, they ensure end-to-end security for blockchain projects—from development to post-deployment.
Powering Shentu is the Shentu Chain, a security-first, delegated proof-of-stake blockchain. It serves as the solid foundation for the future of blockchain security.
Core Features and Applications
Shentu Shield
ShentuShield is a decentralized pool of CTK designed to reimburse lost, stolen, or inaccessible assets across various blockchains. Members of the pool contribute CTK as collateral to cover approved Claim Proposals and ensure funds are available for reimbursement.
The ShentuShield system comprises two key components. First, some members contribute CTK to the pool as collateral providers. Their contributions enable the pool to offer reimbursement for valid claims. Second, there are members who safeguard their crypto assets by reserving a portion of the ShentuShield Pool. By participating, they gain an added layer of protection and the peace of mind that their assets can be reimbursed.
The Security Oracle
Shentu’s Security Oracle’s mission is to give DeFi projects the insight (security score) on whether a potential transaction call is secure or not, thus gaining confidence in the decision to issue such a transaction.
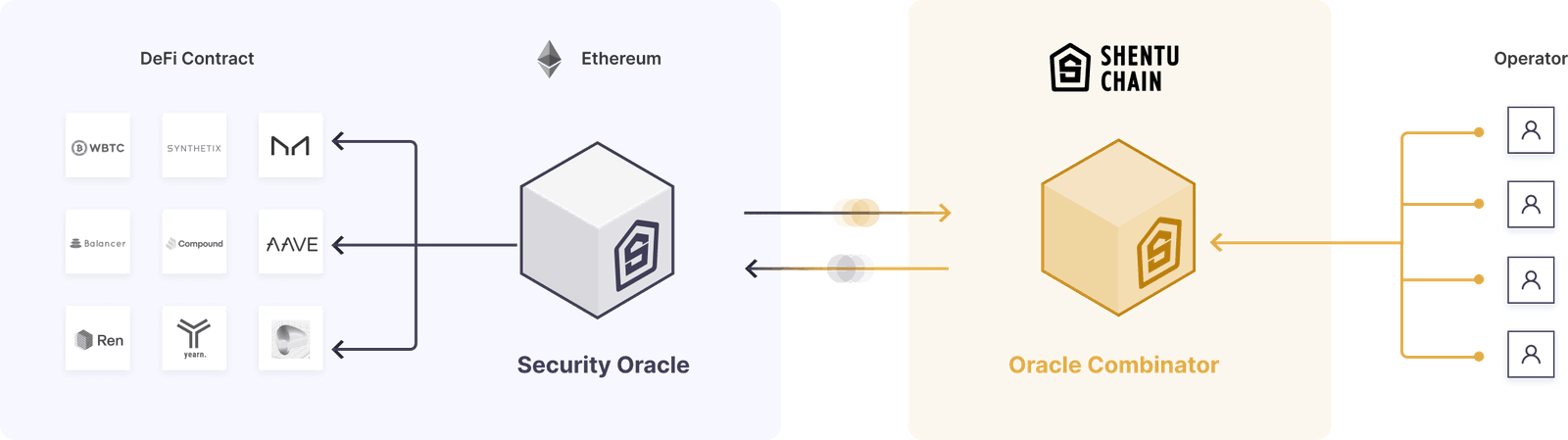
With the Shentu Security Oracle, a decentralized network of security operators assesses source code reliability and earns CTK, the native digital currency of the Shentu Chain. The Security Oracle combines these assessments to create a real-time, on-chain aggregate score that anyone can use to validate contract security. Based on the risk tolerance of users or smart contracts, the security score provides insights on transaction sizes—whether they should be smaller, split, or stopped altogether. The Security Oracle continuously aggregates smart contract security assessments, allowing projects to get their code audited quickly to meet timelines. By leveraging a decentralized group of security operators, the suite of security tools and analyzers grows constantly. New assessments from these tools become part of the continuously updated Security Oracle score.
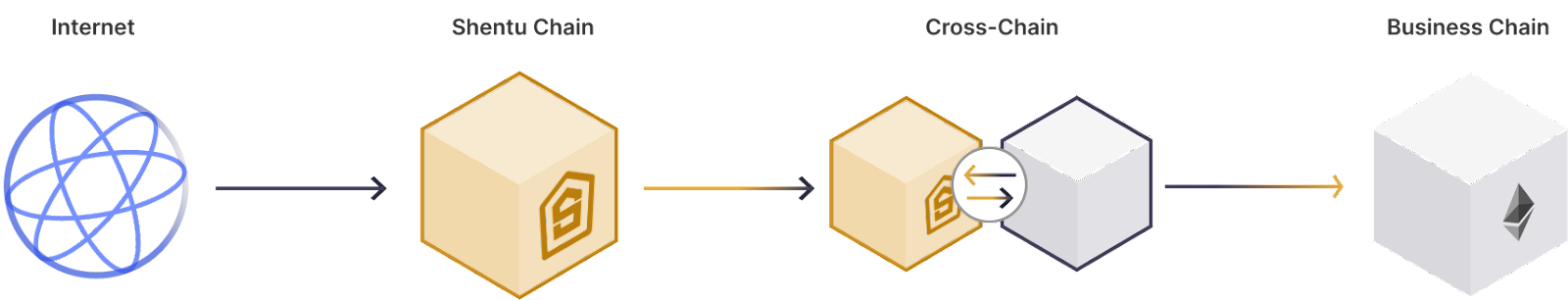
There are multiple components to the Shentu Security Oracle, which work together to create a robust and reliable Security Oracle network, ensuring the integrity and safety of smart contracts:
- Business Chain: The targeted blockchain platform, Ethereum, where Shentu Chain provides the Security Oracle. This chain includes a security oracle interface that accepts security inquiries from DeFi applications for upcoming transactions.
- Shentu Chain: The underlying blockchain that handles security inquiries from Business Chains, offering various components to address security problems. The Shentu Chain has two main elements:
- Oracle Combinator: Built-in frameworks from Shentu Chain that enable decentralized and transparent Oracle workflows, including task management and result aggregation
- Security Primitive: Platform for Security Providers to register on-chain services or off-chain API endpoints as diverse functionalities that address security considerations.
- Cross-Chain: Communication and interaction components maintained by the Shentu Security Council, facilitating connections between different chains. The cross-chain component consists of the following:
- Oracle Operator: Individuals who register as Oracle Operators on Shentu Chain, running and maintaining software to contribute to the network.
- Oracle Syncer: Cross-Chain component owned by Shentu Chain's Security Council, facilitating data synchronization between Security Oracle events on Ethereum and Shentu Chain.
Finally, the last component is the off-chain internet, the Traditional Web 2.0 environment where security scans and analysis occur. Oracle Operators can access security insights and proprietary technologies using tools and communication protocols like HTTP/RPC.
DeepSEA
DeepSEA is a functional programming language that empowers developers to tackle intricate code while ensuring verification through the Coq proof assistant (a formal proof management system that provides a language to write mathematical definitions, executable algorithms, and theorems). Initially tailored for building systems software like OS kernels, DeepSEA utilizes the same features to encapsulate the state within a kernel to implement smart contracts in the blockchain realm.
The aim is that with DeepSEA, developers access a streamlined solution that automatically generates executable code and a formal model, which can be seamlessly loaded into the Coq theorem prover. This integration between smart contracts and Coq enables users to apply Formal Verification to even the most demanding tasks, resulting in a fully verified program that instills confidence.
Shentu Governance and CTK
A robust governance model and consensus mechanism are at the heart of Shentu Chain's decentralized ecosystem. Powered by the native digital asset $CTK, the platform enables token holders to actively participate in shaping its future. Through a decentralized governance framework, CTK holders can propose and vote on protocol upgrades, parameter adjustments, and resource allocation. This democratic approach ensures community involvement, transparency, and collective decision-making.
Furthermore, Shentu Chain utilizes a secure and efficient delegated Proof-of-Stake (DPoS) mechanism, where CTK holders elect block producers to validate transactions and secure the network. DPoS is a verification of the Proof-of-Stake mechanism, in which stakeholders can build consensus according to the amount of stake in the blockchain. What makes DPoS interesting is that it values scalability and speed, and comes with the additional advantage of being able to streamline digital transactions. However, the model also has one obvious flaw, it favours those who hold the most assets. Thus, to keep the network more decentralized, it is important that delegators spread their stake across multiple validators.
Final Thoughts
Shentu Chain is taking the initiative to change security and trust within the Web3 landscape and off-chain. With its comprehensive solution package, including the ShentuShield reimbursement pool, the Security Oracle, and the secure programming language DeepSEA, Shentu Chain aims to ensure end-to-end security for blockchain projects. Its DPoS consensus mechanism and governance model, fueled by the digital asset CTK, fosters active community participation and collective decision-making, establishing it as a decentralized and inclusive platform. By combining technology solutions, transparent governance, and a commitment to provable trust, Shentu Chain is well-positioned to elevate the standards of security and reliability in the blockchain industry.
Stakin has been operating on Shentu Testnet since July 2020 and has been operating on Shentu Chain Mainnet since October 2020. We collaborate with the Shentu team and external stakeholders to provide security and solid infrastructure for the chain and look forward to continuing to do so to improve trustworthiness and security in the blockchain.
For more information about Stakin, visit the Website, Twitter, Blog, or join the Telegram and Discord community.
DISCLAIMER: This is not financial advice. Staking, delegation, and cryptocurrencies involve a high degree of risk, and there is always the possibility of loss, including the failure of all staked digital assets. Additionally, delegators are at risk of slashing in case of security or liveness faults on some protocols. We advise you to do your due diligence before choosing a validator.



