Staking is a popular way to earn rewards while supporting blockchain networks, but security remains essential. You can participate in non-custodial staking while maintaining full control of your tokens. In this article, you’ll learn:
- What staking is and why security matters
- How staking has evolved: from custodial to non-custodial
- Best practices you can follow to ensure safe staking
- How Stakin operates securely as a validator
Whether you're new to staking or looking to deepen your understanding of non-custodial staking security, this guide will give you the key insights you need to stake with confidence and security.
What is staking, and why does security matter?
Staking is a key feature of many blockchain networks, allowing token holders to participate in securing the network, validating transactions, and earning staking rewards. By staking your tokens, you contribute to a blockchain´s stability and decentralization, ensuring that the network remains resilient and operates without centralized control. For many participants, staking is also an opportunity to generate passive income while supporting the growth of blockchain ecosystems. However, staking security is critical, ensuring that your tokens remain safe while you earn rewards is a top concern for delegators and network participants.
From custodial to non-custodial staking: how things have evolved
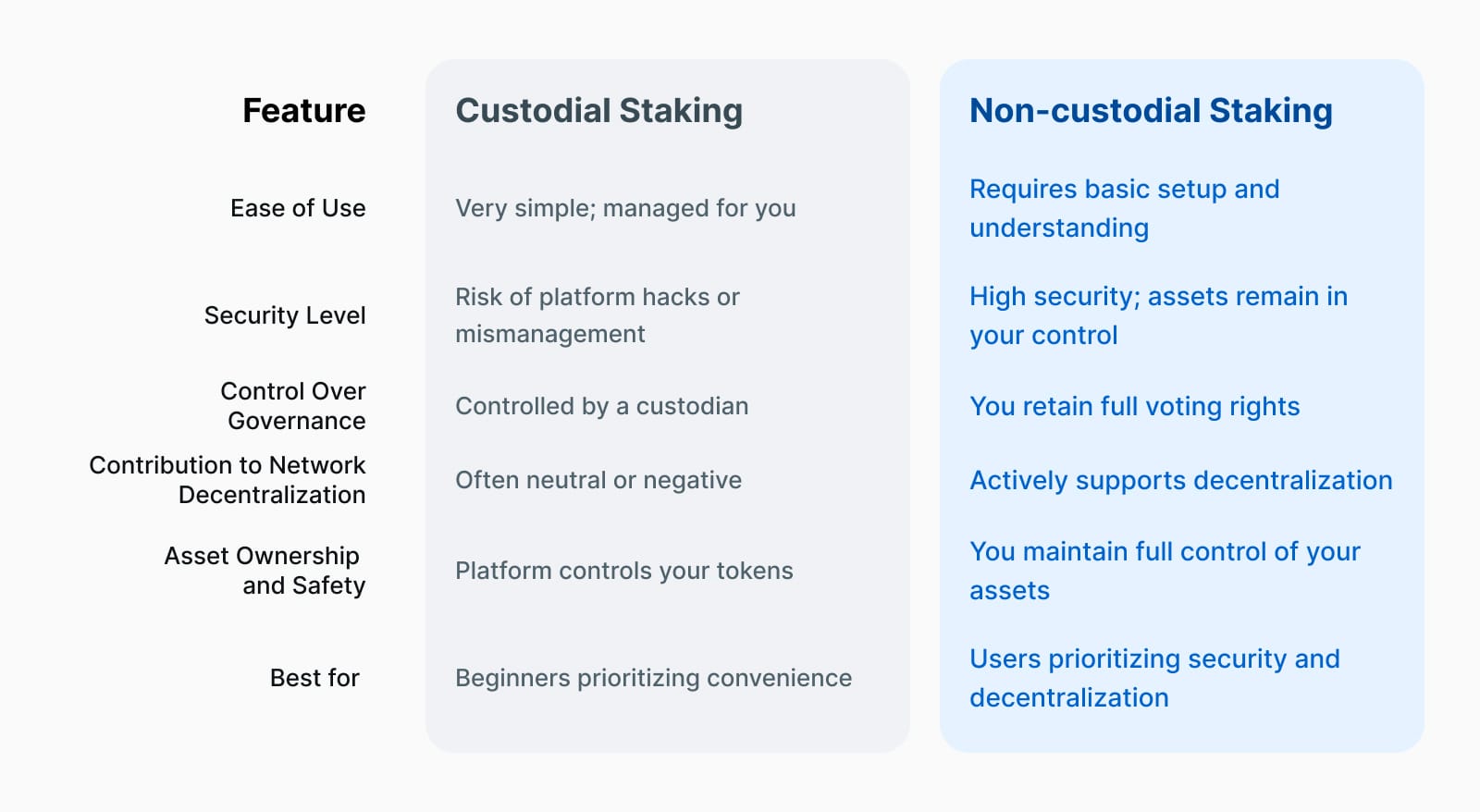
In the early days of staking, it was typically offered through custodial providers, centralized platforms (such as exchanges) that took control of your tokens and managed the staking process on your behalf. While this approach offered convenience, it also introduced significant risks: custodians hold your private keys, meaning you lose direct control over your assets. If the custodian is compromised, mismanages funds, or faces internal issues, your tokens could be at risk.
Non-custodial staking offers an alternative for those who prefer not to rely on third parties. It generally takes two forms:
- Running your node requires a significant upfront investment, technical expertise, and ongoing maintenance to function properly as a validator.
- Delegating your tokens to a validator is a much simpler and more accessible option for most users.
It’s likely for these reasons that non-custodial staking has become the preferred method for many today. Instead of handing over your tokens, you delegate your staking or voting power to a validator like Stakin while keeping full control of your assets in your wallet. Your tokens never leave your possession, which significantly reduces the risks associated with hacks, fraud, or custodial mismanagement.
This self-sovereign approach aligns with the core principles of decentralization and personal asset control in the crypto space. It allows you to earn rewards across various protocols and tokens while maintaining ownership of your assets. With non-custodial staking, you get the best of both worlds: the security of holding your tokens in your wallet and he opportunity to earn staking rewards by supporting the networks and validators you trust. This model empowers users to engage in the staking ecosystem while staying true to the decentralized ethos of blockchain technology.
Why Stakin prioritizes security in non-custodial staking
At Stakin, we know that delegator security is paramount. When you trust us as your validator, you maintain ownership of your tokens, but we ensure your staking experience is secure and seamless. We've created this comprehensive guide on non-custodial staking security to help you understand how this model protects your assets and what best practices for staking you can follow to maximize safety.
How does non-custodial staking keep your tokens safe?
Non-custodial staking ensures your tokens remain secure because you never give up control of your private keys. Instead of transferring ownership to a third party, you delegate your staking power to a validator while your assets stay in your wallet.
This significantly reduces risks such as hacks targeting centralized custodians, mismanagement of funds, or custodial failures and insolvency. By retaining full ownership of your tokens and only delegating the rights needed to participate in staking, non-custodial staking aligns with the core principles of decentralization and personal asset control. It allows you to earn staking rewards while ensuring that your crypto remains secure in your wallet.
Best Practices for Safe Staking: How to Protect Your Tokens and Maximize Rewards
Even though non-custodial staking keeps your tokens secure in your wallet, following some staking best practices will help you stay safe, maximize rewards, and avoid common risks. Here’s what every delegator should know:
- Use a Hardware Wallet for Extra Security
For the safest staking experience, use a hardware wallet (like Ledger or Trezor). Hardware wallets store your private keys offline, protecting them from online threats like hacks, phishing, or malware. This adds an extra layer of staking security. - Choose a Trusted Validator with Strong Security
Choosing a trusted validator with strong security measures is crucial for safe non-custodial staking. Select a validator that prioritizes security, performance, and transparency. For example, a validator like Stakin, with ISO 27001:2022 certification and robust infrastructure, helps ensure your staking rewards remain secure from risks like downtime or slashing penalties.
- Understand the Network’s Slashing Risks
Different blockchain networks have their own staking rules. Some may penalize validators (and their delegators) for actions like going offline or double-signing blocks. Stay informed about the slashing risks and rules of the network you’re staking on. - Monitor Your Staking Positions Regularly
Even though non-custodial staking allows you to earn passive rewards, it's essential to regularly monitor your staking positions to ensure everything runs smoothly. Check that your validator is performing optimally and meeting network standards, and verify that your staking rewards are being received consistently. If your validator's performance declines or you notice irregularities in reward distribution, be ready to redelegate your tokens to a more reliable validator. Staying proactive helps you maximize staking rewards while keeping your assets secure. - Keep Wallets and Apps Updated
Always update your wallet software (whether it’s a hardware wallet, browser extension, or mobile app). Updates often include security patches that protect your assets. - Watch Out for Scams and Phishing
Crypto stakers are frequent targets for scams and phishing attacks, so staying vigilant is essential for staking security. Always use official links when accessing staking platforms or interacting with validators. Never share your private keys or seed phrases with legitimate platforms, and validators will never ask for them. Be especially cautious with offers that seem too good to be true, such as fake airdrops or validator impersonations, as these are common tactics used by scammers to compromise your assets. Staying alert helps protect your staking rewards and maintain control over your tokens.
By following these staking best practices, you’ll keep your assets secure, maximize rewards, and enjoy peace of mind while participating in non-custodial staking.
How Stakin operates securely as a validator
At Stakin, security, reliability, and risk minimization are at the core of our operations as a non-custodial validator across over 40 blockchain networks. Here’s how we ensure that your staked assets remain safe while earning rewards:
- Customized and Isolated Infrastructure
Each blockchain we support operates on dedicated, isolated infrastructure. This means that the performance or issues in one network cannot affect others. We also over-provision resources like CPU, RAM, and storage to handle spikes in network activity. Additionally, geographically distributed sentry nodes help shield our validators from DDoS attacks, ensuring continuous uptime. - Redundancy and Manual Failover
To minimize risks like downtime or double-signing penalties, we maintain redundant validator nodes. If a problem arises, our manual failover process, verified by multiple team members, ensures a secure transition, avoiding the risks of automated errors. - Continuous Monitoring and Blockchain Snapshots
We use 24/7 monitoring systems to detect and respond to any potential issues across all networks. Regular blockchain snapshots allow us to quickly recover and restore validator operations in case of malfunctions, further enhancing the reliability of our services. - ISO 27001:2022 Certified Security
Our Information Security Management System (ISMS) is certified under the ISO 27001:2022 standard, covering everything from organizational processes to technical safeguards. This certification reflects our commitment to high security standards and continuous improvement. - Secure Validator Key Management
Access to our production infrastructure is strictly controlled. Validator keys are stored in encrypted vaults and hardware security devices, accessible only by authorized personnel, ensuring the integrity and confidentiality of all validator operations.
Final Insights
Staking securely doesn’t have to be complicated. With non-custodial staking, you maintain full ownership of your tokens while actively supporting the growth and security of blockchain networks by partnering with trusted validators and following essential staking best practices. You can optimize your staking experience, protect your assets, and earn consistent rewards.
At Stakin, we’re committed to providing a secure, transparent, and seamless staking process so you can focus on what matters most: growing your portfolio and supporting the projects you believe in. Ready to stake securely and take control of your assets? Delegate to Stakin today and start earning rewards with confidence!
DISCLAIMER: This is not financial advice. Staking, delegation, and cryptocurrencies involve a high degree of risk, and there is always the possibility of loss, including the failure of all staked digital assets. Additionally, delegators are at risk of slashing in case of security or liveness faults on some protocols. We advise you to do your due diligence before choosing a validator.



